Chris has seen several Ransom Ware infections in the past 18 months or so. Ransomware is just about the worst of the malwares the “bad guys” have thought up. Essentially, once you get infected, the ransomware installs a nifty little program which encrypts all of your data. Then, they’ll give you a pop-up letting you know that you have so much time to pay a ransom to receive the encryption key.
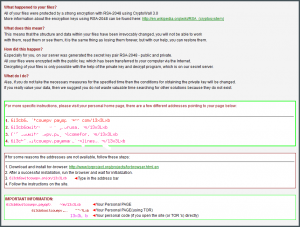
Here is a screen shot of one of the ransom notes Chris has seen.
I’ve asked Chris to tell you what ransomware looks like, what you can do if you’re infected, and how to protect yourself.
I’ve seen three actual instances of ransomware in the past few years.
The first instance occurred about two years ago at a customer site. I found that their personal and business files were all encrypted. Since they had a fairly recent backup of their data, the thought process was relatively quick: remove the old hard drive, install a new one, rebuild their server, and restore their data. This took several hours to complete, but it was successful and very little data was lost.
The previous instance occurred last summer, to a customer I hadn’t served in many years. I forget the nature of the problem which motivated the service call, but I soon discovered that their personal data was unreadable. I turned off the computer and removed the hard drive, so that I could see what customer data was there without allowing the infection to proceed if it was still active. Turns out the customer already had a secondary infection which had been running for the past six months. This created a huge volume of temporary files and greatly delayed my getting permission to access to their data. Somewhat fortunately, every personal folder which had been encrypted had had a text file and an HTML file added, which contained a document from the ransomware software. The document indicated that the data was encrypted, and if you wanted to get it back you had pay a fee in BitCoin at one of 4 different IP addresses. Note that only one IP address was responsive. The ransom cost started at some amount, and would increase as time went on. To prove that they were indeed the ones which encrypted the data, they offered to decrypt one file immediately and at no charge. In talking with the customer, they identified the one file that was the most critical, and this one file was successfully and promptly decrypyted. Eventually, the customer decided to pay the ransom, which was about $700. It it took a long time for the customer to get the BitCoin payment into a spendable account, and then the payment could not be given because none of those IP addresses were accessible. We were ultimately declined access to provide the ransom payment because their servers were too busy to receive another connection. Apparently their servers were being crushed with activity from their own success.
The most recent occurred a few months ago at a business I frequent. The symptom to them was that the computers which run their business management application displayed an error message saying that the database was corrupt. Since I was there at the time this happened, my recommendation was that they turn off all of their computers. Turns out they received an encrypting infection called “Locky”, because the customer files are encrypted and renamed to have a “.Locky” extension. But there was no opportunity to pay a ransom to get the data back. Another problem was that there was no backup of their data for several years. The solution was to replace the old hard drive with a new drive in the server computer, reinstall and update the operating system, and coordinate with the manufacturer to reinstall the application and look for old data. Fortunately, a copy of the database that was 6 months old was found; so there was a 6 month gap in time, but at least they had not lost 20 years of customer data. Also, a good antivirus was installed on all of their computers, which they did not have before. They did not understand that they needed a good antivirus installed. This was actually a problem that was waiting to happen. It could have been avoided if their usual “IT Guy” had taken the initiative to see what they did and did not have, rather than just doing a technical task they were called in to do. They are hopefully in the process of getting a backup procedure, because hindsight showed that having a 6 month gap in customer data could have been avoided if their usual “IT Guy” had implemented backups of their data.
There are lessons to be learned from these experiences.
- Have a good antivirus on all of your technology. Note that there is no antivirus on the planet that can protect you from all things all the time.
- Have your computer prepped by a competent IT person.
- Make backups of your data. Backups never go out of style. It can be to an external hard drive, or a USB thumb drive, or to a cloud based backup service like Dropbox.
- Know the completion status of that backup. I’ve lost count of the number of customers who believe that they have been backing up for long time, but turns out that their data is actually old because the backup has not worked for years.
Chris Eddy of Geek For Hire, Inc. has been providing computer service to families and small businesses with Mac’s and PC’s for the past fourteen years. His company is highly rated by both the BBB (Better Business Bureau) and by Angie’s List. You can find more on our website. Geek For Hire, Inc. provides onsite service (Tier 3) to the Denver / Boulder / Front Range area and remote service throughout North America.
We’ve been using Amazon Prime for the past few years. We like the free 2-3 day shipping and the online streaming. I haven’t tried the Kindle lending library yet, but I’m tempted! Prime is normally $99/year, but you can try it for 30 day for free by clicking on this link: Try Amazon Prime 30-Day Free Trial (Yes, we’ll get a small commission when you sign up.)