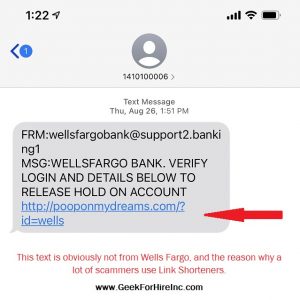
Whether you know it or not, you are a spam risk.
It’s that time of year to be more aware of all the monsters out there. I wish I was just talking about the cute kids in a Frankenstein costume. I’m talking about the scary tech monsters, the phishers, the scammers, the spoofers, and the hackers. And, unfortunately, they don’t just confine themselves to making their mischief around Halloween. These are year-round monsters!
Some of the ways they can attack you include emails, text messages, phone calls, and social media. We’re talking about the Chase text scam, the Publisher’s Clearing House email scam, the Paypal email scam, and the Wells Fargo email scam, just to name a few. These all add up to more spam risk in your inbox.
But first, let’s define some terms:
Contents
Tech Terms Defined:
Scam:
“…an attempt to defraud a person or group after first gaining their trust.” (from Wikipedia)
Hacking
Hacking is when someone uses social engineering to obtain information from you or installs a virus onto your computer or phone. Here is Wiki’s formal definition of a hacker:
“A hacker is a person skilled in information technology who uses their technical knowledge to achieve a goal or overcome an obstacle, within a computerized system by non-standard means. Though the term hacker has become associated in popular culture with a security hacker – someone who utilizes their technical know-how of bugs or exploits to break into computer systems and access data which would otherwise be unavailable to them – hacking can also be utilized by legitimate figures in legal situations. For example, law enforcement agencies sometimes use hacking techniques in order to collect evidence on criminals and other malicious actors. This could include using anonymity tools (such as a VPN, or the dark web) to mask their identities online, posing as criminals themselves.” (from Wikipedia)
Spoofing:
“Email spoofing is the creation of email messages with a forged sender address.” (from Wikipedia)
“Caller ID spoofing is the practice of causing the telephone network to indicate to the receiver of a call that the originator of the call is a station other than the true originating station. This can lead to a caller ID display showing a phone number different from that of the telephone from which the call was placed.” (from Wikipedia)
For example, I got phone calls from a Denver physician and “Account Services” last week. When I answered, the recorded voice wanted to sign me up for an extended warranty for my car.
Also, when you get a spammy email “from” yourself, someone has spoofed the message to make it appear that it is coming from you.
We’ve also seen emails from CustomerService@Amazan.com. This is not technically spoofing, but at first glance, you do think the email is coming from Amazon.
Phishing:
“Phishing is a type of social engineering where an attacker sends a fraudulent (“spoofed”) message designed to trick a human victim into revealing sensitive information to the attacker or to deploy malicious software on the victim’s infrastructure like ransomware.” (from Wikipedia)
I’ve created a Free Report to protect you from “phishing” scams. Click here to receive it.
SpearPhishing:
“Spear phishing involves an attacker directly targeting a specific organization or person with tailored phishing emails. This is essentially the creation and sending of emails to a particular person to make the person think the email is legitimate. In contrast to bulk phishing, spear phishing attackers often gather and use personal information about their target to increase their probability of success of the attack.” (from Wikipedia)
How Can You Protect Yourself?
Whenever you receive a text, email, or phone call, take a minute to think before responding. Here are our suggestions to protect yourself from spam risk:
Email Scam:
If you’re like me, you receive multiple emails every day asking you to do something. How to tell if an email is fake? There are several steps that you should follow:
- First, make sure the message is actually from the person or organization that it says it is from. Look at the email address to make sure it is correct and not subtly different. (For example: Amazan instead of Amazon, or J0hn instead of John. In one case I exchanged an “a” for the letter “o”, in the second case I exchanged the number “0” for the letter “0”.)
- If you reply, you should also scrutinize the “To” address. If your friend’s email has been hacked, the “To” address may go somewhere totally different.
- Don’t click on any links in an email. If it is a company telling you that you need to contact them by clicking this link, call or email them using information that you already have. If it’s from a friend, ask them to confirm that they have actually sent you something.
- Never click on short links like bit.ly, TinyURL, ow.ly, etc. It is too easy to hide malware in a link that appears to come from a legitimate source. (More about URL shorteners.)
- Do check your spam folder in your email every week to 10 days to make sure a friend’s email didn’t get sent there by accident.
Phishing Text Scam:
Text messages have become a more common way for scammers to attack. Sometimes they’ll send it just to you, and sometimes it will be a group text. When you look at those group texts, you might notice that they all have a similar phone number to you. Here is just one of the spam risk text messages I’ve received. Remember that the phone company is not going to reward you for paying your bill:
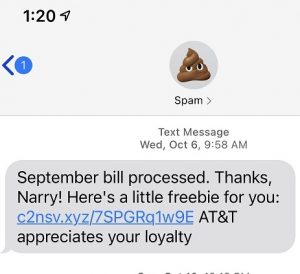 Here’s an image of the Wells Fargo text scam. It’s my favorite scam text:
Here’s an image of the Wells Fargo text scam. It’s my favorite scam text:
I haven’t received a scam message from a known contact yet. I’m sure that more sophisticated text scams are coming. Just be careful before replying to any text message.
Bogus Phone Calls:
Phone calls are where we are seeing the most issues. You receive a phone call and the person on the other end sounds legit. They create an urgency about a virus on your machine or an unauthorized charge on your bank card. Whatever it is, they’ve convinced you that you need their help RIGHT NOW! So you confirm your date of birth or give them access to your computer.
I’ve found that the best thing to do is to never answer phone calls from someone I don’t know. If it’s a real person, they’ll leave a voice mail. Even if it’s not a real person and they leave a voicemail, I can tell it’s not someone I want to call back.
If you do answer a call like this and don’t realize right away that it is a scam, the best policy is to never provide personal information or allow them access to your computer.
Studies have shown that older people are more trusting in general, and tend to get hacked more frequently. (Malwarebytes 9/2021 Report, LexisNexis 7/2021 Report) So, if you’re “of a certain age”, be extra careful about providing information to someone you don’t know.
- If they say they are from your bank, tell them that you’ll call your bank on the number you already have in your contacts to confirm what they’re telling you.
- If it’s “Microsoft” or “Apple” or “Dell” calling to tell you that there is a virus on your computer, thank them and hang up. Then run your virus scanner just to be on the safe side. You’ll get a call from a friend saying you’ve been hacked before a major corporation will let you know!
Social Media:
I’ve written several articles about hacked Facebook (and Social Media in general). Check them out here, here, and here.
Information About Geek For Hire, Inc.
Chris Eddy of Geek For Hire, Inc. has provided computer service to families and small businesses with Mac’s and PCs for the past eighteen years. Angie’s List and the BBB rate Geek For Hire very highly. You can find more on our website, or give us a call at 303-618-0154. Geek For Hire, Inc. provides onsite service (Tier 3 support) to the Denver / Boulder / Front Range area and remote service throughout North America.
Here’s a link to our Covid19 Policy.
We’ve been using Amazon Prime for the past few years. We like the free and fast shipping. With Prime, we have access to online streaming too. Prime is usually $119/year, but you can get a free 30-day trial by clicking on this link: Try Amazon Prime 30-Day Free Trial. As an Amazon Associate, we earn from qualifying purchases.
More Tips Here:
- Thinking about buying a personal computer?
- … or about getting a new Mac?
- Ready for the DSTime change?
- Has your email been hacked?
- And here are the 10 Password Mistakes you don’t want to make!