Last week I attended Microsoft’s “Virtual” Security Summit. I have the word virtual in quotes because I didn’t have to travel anywhere. My son and I watched the live streaming video in our living room! While I like the buzz of meeting new people, staying at home and learning new things has its advantages as well. The Summit was primarily targeted towards management of large enterprise firms, I did pick up a few nuggets of information that will help the average person with the security of their machine as well.
First tip for Security: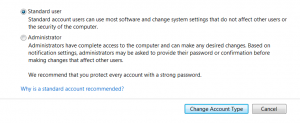
Make sure the user permissions on your account are set to “Standard User” and not “Administrator”. This cuts down on the chance that viruses or other malware can be easily installed on your machine. This also protects a random bad operator from installing a bitcoin mining operation on your machine. You provide the computer and electricity, they get the benefit. If anyone has ever installed the SETI program on their machine, it would work similarly to that. (The “Search for Extra-Terrestrial Intelligence” program gave the opportunity for ordinary computer users like Chris Eddy to allow SETI to use some of their computer operating power.)
Next:
Make your machine harder for the bad guys to get access to. Use a very secure password, set up two-factor authentication wherever you can. Install updates to your Operating System as soon as they are available.
Finally:
Use good security practices. Patti Chrzan, head of Microsoft’s cyber-security fraud division said this:
“90% of all cyber crime starts with a phishing email”
A reminder that the phishing email is an attempt to get access to your personal information, like your birthday or password. A phishing email might also install a virus, ransomware, or other malware.
Being hyper-alert of every click, and every email you open puts you way ahead of the average person. Even if the email seems legit, never click on a link in an email from a corporation until you have confirmed its legitimacy. Call the company to confirm that your account has been hacked, or your password was changed, or a large purchase was made. Never take the word of an email at its face value!
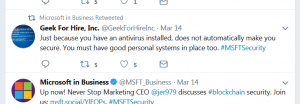
The highlight of my day was when Microsoft retweeted my comment:
Just because you have an antivirus installed, does not automatically make you secure. You must have good personal systems in place too.
Past blogs you may find helpful:
- 20 February 2018 – Secure Passwords
- 28 November 2017 – Phishing
- 4 April 2017 – Two-Factor Authentication
Information about Geek For Hire, Inc.
Chris Eddy of Geek For Hire, Inc. has been providing computer service to families and small businesses with Mac’s and PCs for the past eighteen years. Angie’s List and the BBB rate Geek For Hire very highly. You can find more on our website, or give us a call 303-618-0154. Geek For Hire, Inc. provides onsite service (Tier 3 support) to the Denver / Boulder / Front Range area as well as remote service throughout North America.
We’ve been using Amazon Prime for the past few years. We like the free and fast shipping. With Prime, we have access to online streaming too. Prime is usually $119/year, but you can get a free 30-day trial by clicking on this link: Try Amazon Prime 30-Day Free Trial. As an Amazon Associate, we earn from qualifying purchases.