Lately, my inbox has been overrun with cries for help. Folks are telling me that their Facebook account has been hacked! The hackers are out there using a little social engineering to figure out your password and get total control of your Facebook.
- “Someone hacked my Facebook and changed my password”
- “Someone hacked my Facebook and changed my password and email”
- “I was hacked on Facebook Messenger”
- “My Facebook keeps getting hacked”
- “Opened message from hacked Facebook account”
And, my favorite:
- “My ex hacked my Facebook Can I press charges?”
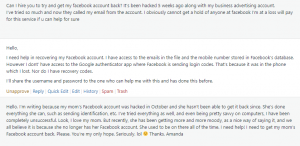
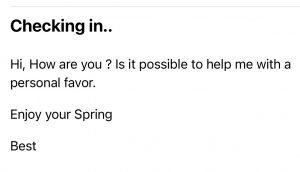
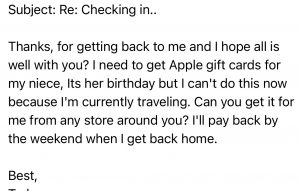
Here’s just a small sample of some of the messages I’ve received:
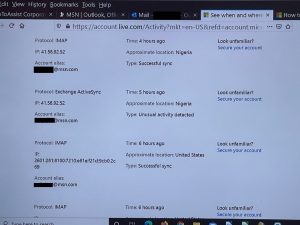
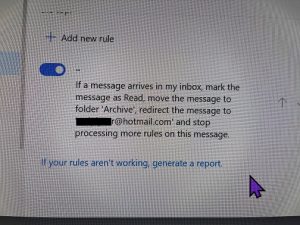
Unfortunately, once you’ve lost control of your Facebook account, it’s awfully hard to get it back. We’ve tried to get accounts back, but, the hackers know what they’re doing. Once they take control, they lock the account down pretty tightly. They have already proved to Facebook that they are you, and once they’ve changed the email address and phone number, you’re not going to get it back.
What should you do right away if your Facebook account has been hacked, your password and email are changed, and you’ve lost control of it?
There are a number of things you should do right away. Think about your finances, online security for other accounts, your email, and other personal data like photos and notes.
What if my credit card or bank account is connected to my Facebook account?
The first thing you should do is contact your bank. If you have your credit card, debit card, or bank account connected to your Facebook you should cancel them right away. Period. Don’t even think about this. If the hacker has full control of your Facebook, they can go on a spending spree with your money. Until your bank officially cancels the card, keep a very close eye on your online banking activity.
Should I change my password on other accounts?
When your Facebook account has been hacked, you should change the password on these accounts right away:
- Change the password on your email. If your Facebook uses multiple emails, change it on all of those accounts
- Any account where you are using the same password as Facebook
Once you’ve changed the password on your email and any account using the same password as Facebook, change the passwords on all of your other accounts. (Yes, I said ALL!)
We recommend that you change your password on social media and your financial accounts at least monthly. Use a password that is at least 12 characters. (Longer is better.) Here’s an old blog on how to create a secure password that you’ll remember.
Use something like: “MyNewF@ceb0okPW!”, or “NewFB@ccount1nfo”. Both are 16 digit passwords. Notice that there is a mix of capital and small letters, numbers, and special characters. (I’ve replaced the “A”s with the @ symbol, one of the “o”s of Facebook is actually a zero, and the “I” of Info is actually the number one.) Change it at least once a month going forward.
Can they hack my email too?
Double-check your email settings. Have they changed? You should look especially at the “Reply-To” address. And change your password too!
I’ve been using Facebook to log into other apps. How do I get into them now?
If you’ve used another way to log into those apps, you can probably still log in with a password reset. If you only used Facebook to log in, you may be out of luck. Contact Customer Service for the app. Let them know what happened and tell them your email. They may let you back in. Since Instagram is owned by Facebook, you’ll probably have difficulties there.
I’m embarrassed. Should I tell my friends?
Absolutely! After you speak to your bank and change your password, call your friends. They should be on the lookout for messages that are not from you, especially if the message is asking for help or money.
How do I get all my photos back?
If you set up your account as “Public”, and the hacker hasn’t changed the settings, you may still be able to get access to your photos, albums, notes, etc. If you can’t, ask someone you trust (who is still a “friend” of the account) to download all of your data.
What about my Facebook business account?
If you’ve lost access to your personal Facebook account, you’ve lost access to your business account too. Make sure your customers know. If you’ve ever purchased advertising on Facebook, contact your bank and cancel that card or account.
Setting up a new Facebook account:
What should I do to securely set up a new personal Facebook account?
- Set up a new email account to use only for Facebook
- Set up Two-Factor Authorization with the new account.
- Make sure your password is at least 12 characters long and contains a good mix of numbers, letters, capitals, and special characters.
- Go through the Privacy and Security settings on your new Facebook and lock it down as much as you can.
- Change the password on your new account monthly.
- Don’t provide any financial information to Facebook. If you want to purchase something on the Marketplace, negotiate a different means of payment with the seller.
How should I set up a new Facebook Business account?
- Create another new email account to only use with your Facebook business account. (You’ll need to set up a personal account first. And, yes, you’ll end up with two personal accounts.)
- Follow the same steps outlined above for setting up your new business account.
- If you advertise on Facebook, ask your bank for a separate credit card with a minimal spending limit. (Don’t use a debit card!)
How do I “Lock Down” my new account(s)?
If figuring out the Privacy settings on your new Facebook page is more than you want to do, let us know. We can set up a remote appointment with Chris to go through all of your settings to make sure another hacking is less likely. (Unfortunately, there are never any guarantees when it comes to protecting yourself from hackers.)
Information About Geek For Hire, Inc.
I’ve created a Free Report to protect you from “phishing” scams. Click here to receive it!
Chris Eddy of Geek For Hire, Inc. has provided computer service to families and small businesses with Mac’s and PCs for the past eighteen years. Angie’s List and the BBB rate Geek For Hire very highly. You can find more on our website, or give us a call at 303-618-0154. Geek For Hire, Inc. provides onsite service (Tier 3 support) to the Denver / Boulder / Front Range area and remote service throughout North America.
Here’s a link to our Covid19 Policy.
We’ve been using Amazon Prime for the past few years. We like the free and fast shipping. With Prime, we have access to online streaming too. Prime is usually $119/year, but you can get a free 30-day trial by clicking on this link: Try Amazon Prime 30-Day Free Trial. As an Amazon Associate, we earn from qualifying purchases.
More Tips Here:
- Are VPNs worth it? More here.
- Are you interested in learning more about Extreme Privacy?
- We have seen a lot of Facebook hacking lately. Here’s what you should do ahead of time to keep your account safe.
- And here are the 10 Password Mistakes you don’t want to make!