This past week, we received hacked email messages “from” several different customers indicating that their email account has become compromised. I have “from” in quotes because the emails weren’t actually from those people.
Each email was similar, in that they all started with a benign and short email message saying “Checking in” or “Favor to ask!” or “Hey there?”. The request said something like “I wonder if I could ask your help?”. All the messages were received within the past 7 days. This indicates an active and fruitful attack that is going on right now.
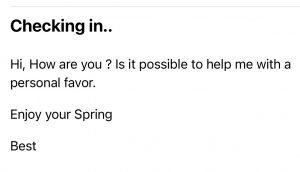
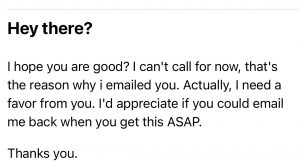
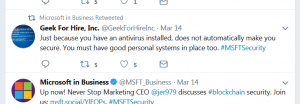
HACKED EMAIL – CHECKING IN:
Here’s a screenshot of one of the first hacked email messages we received:
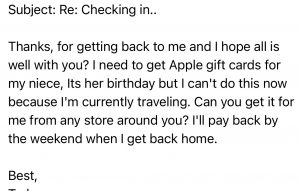
Chris replied with a quick email that said “Yes, I will call you later today”. Our “Spider-Sense” was tingling about this message – because this is not something that this customer would do via email. A few minutes later, we received this message:
We noticed that the “reply from” address was slightly different from his actual email address. (An “R” was added to the end of his name.) I called the customer a few minutes later, and he said he had not sent either of the messages. We talked for a while, and I recommended that he turn off his computer, and wait until I could arrive later that day.
Super-Geek To The Rescue:
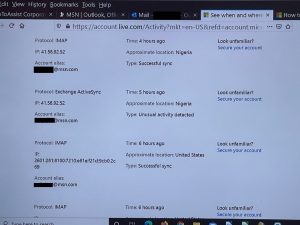
The first thing was to review his MSN account security information, such as the cell phone and alternate email addresses on file which can be used for account recovery, and to change his password. I enabled a feature to disconnect all already connected email programs which might still be connected. We wanted to make sure the hacker did not still have access to his account, to possibly seize back control. I looked through his past login history and found that there were several recent attempts from Nigeria using Exchange. This was a smart and sneaky attack.
I scanned his machine, and found the machine was not infected – but there was something wrong with his MSN email account. His Inbox showed that it had not received any new email messages for the past several days. (He could send email messages just fine.)
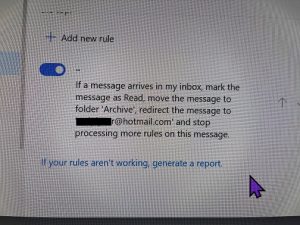
I looked through his account configuration within MSN, and found that a Rule (which did not have a name) had been added. It was applied to every new email message.
- Mark the message as Read
- Move the message to the Archive folder
- Forward a copy of that email message to a different email account. This looked like the customer’s email address but with very subtle differences.
I found that all of the customer’s recent email was indeed in the Archive folder, and moved them back to the Inbox. I deleted the Rule added by the Hijacker.
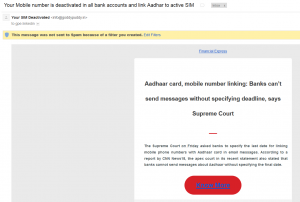
HEY THERE?
Here’s another hacked email we received:
This was a sneaky one too with multiple Rules added to their email. In this case, their Comcast email account had been modified to have a similar Rule added, which was forwarding a copy of all email messages to a similarly named email address under the Hotmail.com domain that did not belong to the customer. The password was changed, the account recovery information was reviewed, and the silent email forwarding Rules (there were two) were found and deleted.
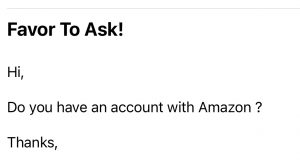
FAVOR TO ASK!
For another customer, we received this “Favor to Ask!” message:
We contacted them with a different email to let them know. They sent an email blast to their contacts announcing that their email address had been compromised, which is good. But they didn’t BCC everyone so we:
- saw their complete list of contacts, and
- so did everyone else.
Remember, if you need to send an email message to many contacts, follow good Netiquette and don’t use CC. Using BCC will hide all contacts that you are sending to. (Who remembers “carbon copies”, “blind carbon copies”, and getting their fingers all inky?!)
FAVOR TO ASK?
We also received this similar message from a hacked email:
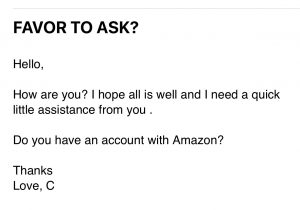 Again, the hacker changed the rules within their email account.
Again, the hacker changed the rules within their email account.
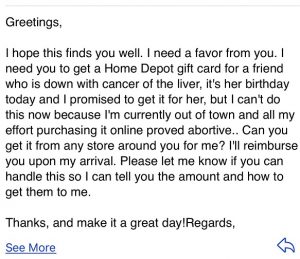
GREETINGS
And, last but not least, we received this convoluted request:
WHAT TO LOOK FOR IN YOUR EMAIL INBOX:
If you get an email like this, it’s important to let the person know, WITHOUT using the email address that was used to send the original message! The best option is to call or text them. If you don’t have their phone number, see if you have another email for them. You can also contact a family member and ask them to pass on the message. I’ve even resorted to sending the person a message on Facebook.
WHAT TO DO IF YOU’RE DEALING WITH A HACKED EMAIL ACCOUNT:
If you find out that your email has been compromised there are several things you should do right away:
- Change your password on your email account.
- Double-check that your “reply to” address is really your address. Look for an extra letter. Is the domain correct? (Comcast? Gmail? Outlook? etc.)
- Check your email account “Rules” to see if any new emails are forwarded to a different address?
- Let people know that your email is compromised. Make sure they know you’re fine and don’t need a gift card for Amazon or Apple. If you send one email to a bunch of people, please use BCC.
As always, if you need help, give us a call. In most cases, we can help you remotely.
CONCLUSION:
Scammers, hackers, hijackers, and spear-phishers are getting more sophisticated in their attacks. Here’s a recent article about a big-time Nigerian email scam. Today is a great day to run your virus scanner, change passwords, set up two-factor authorization, and back up your data!
I’ve created a Free Report to protect you from “phishing” scams. Click here to receive it!
Information about Geek For Hire, Inc.
Chris Eddy of Geek For Hire, Inc. has provided computer service to families and small businesses with Macs and PCs for the past eighteen years. Angie’s List and the BBB rate Geek For Hire very highly. You can find more on our website or give us a call at 303-618-0154. Geek For Hire, Inc. provides onsite service (Tier 3 support) to the Denver / Boulder / Front Range area and remote service throughout North America.
Here’s a link to our Covid19 Policy.
We’ve been using Amazon Prime for the past few years. We like the free and fast shipping. With Prime, we have access to online streaming too. Prime is usually $119/year, but you can get a free 30-day trial by clicking on this link: Try Amazon Prime 30-Day Free Trial. As an Amazon Associate, we earn from qualifying purchases.
More Tips Here:
- Are you interested in learning more about Extreme Privacy?
- We have seen a lot of Facebook hacking lately. Here’s what you should do ahead of time to keep your account safe.
- And here are the 10 Password Mistakes you don’t want to make!