There was another article this week about Location Privacy and “Services” on your smartphone. I have services in quotes because I don’t think the entity being served is the person using the phone.
According to this article, Smartphone applications can and do gather and collect location information on individual smartphones. Then they sell that data. Marketing firms can find out who is in the ER and sell that list to Legal Firms, or who is at Victoria’s Secret and sell it to Macy’s. Privacy, especially location privacy is on its way out.
Most smartphone users don’t really lock down their security settings, sticking with the default settings that came with the phone. When they add a new app to their phone, they may not think to check what data they are sharing with the app developer. When the app asks if they can access the user’s location, they may think it makes sense to share their location, without know what the app will do with that raw data.
What do Marketing Firms really need to know?
As I read through the article, I found the whole thing very disturbing. Should anyone really know that one woman, a middle school teacher, went hiking, goes to the gym, visited a dermatologist, and stayed overnight in another home? While location data is supposed to be anonymous, the specificity of the data means that companies are able to track the location of a smartphone down to the minute. From the article:
“Elina Greenstein, an executive at the location company GroundTruth, mapped out the path of a hypothetical consumer from home to work to show potential clients how tracking could reveal a person’s preferences. For example, someone may search online for healthy recipes, but GroundTruth can see that the person often eats at fast-food restaurants.”
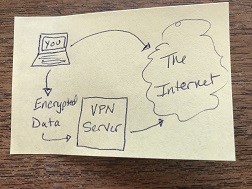
By tracking the smartphone, you can track the person. If you can connect the smartphone location to home and work, you can figure out the person, and track all of their other activities.
Why would you want to share your location information?
There are lots of reasons to share your location. Getting good traffic information is one. Getting the weather is another. But once you’ve checked the forecast, do you really want The Weather Channel (owned by IBM) to continue tracking your location?
What should I do?
I take location privacy very seriously, so here’s what I do. About once a month I go through my list of apps and see which I’m sharing my location with. I turn off location sharing for any apps that don’t need my location to provide a service; social media accounts for example. Then I make sure that I am only sharing my location with apps /WHILE THAT APP IS IN USE/. (I do need to remember to close down the app when I’m done.)
How do I ensure my location privacy?
For the iPhone, click on the “Settings” icon, then scroll down to “Privacy”. Click on “Location Services”, and then scroll through each of your apps.
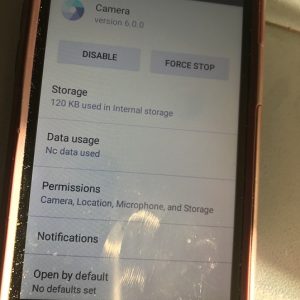
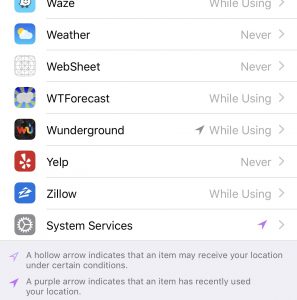 I borrowed a friend’s Android phone to see how she would do this. Again, click on “settings”, then “apps”. At that point, you need to open each app to adjust the location sharing setting. Once you’ve opened the app, click on “Permissions” and adjust the location privacy settings.
I borrowed a friend’s Android phone to see how she would do this. Again, click on “settings”, then “apps”. At that point, you need to open each app to adjust the location sharing setting. Once you’ve opened the app, click on “Permissions” and adjust the location privacy settings.
Please forward this to your colleagues to help keep their online privacy safe too. Did I forget some critical advice, or do you have questions? Let me know in the comments below.
Information about Geek For Hire, Inc.
Chris Eddy of Geek For Hire, Inc. has been providing computer service to families and small businesses with Mac’s and PCs for the past eighteen years. Angie’s List and the BBB rate Geek For Hire very highly. You can find more on our website, or give us a call 303-618-0154. Geek For Hire, Inc. provides onsite service (Tier 3 support) to the Denver / Boulder / Front Range area as well as remote service throughout North America.
We’ve been using Amazon Prime for the past few years. We like the free and fast shipping. With Prime, we have access to online streaming too. Prime is usually $119/year, but you can get a free 30-day trial by clicking on this link: Try Amazon Prime 30-Day Free Trial. As an Amazon Associate, we earn from qualifying purchases.